Digital lives nowadays leave innumerable trails of data. With each click, the digital footprint of a person only grows larger. Everybody gets concerned about the things they do online. The is truth that the internet will never forget what you do online. It does not matter how long the data stays visible. It could be companies that track every single move you make online, thus, erasing digit your footprint is important.
A recent research unveiled alarming privacy issues. Approximately 86% of Americans have actually attempted to erase their information away from the face of the internet, because of the digital footprint. This shows the heightened awakeness. People want the “control” of their own data. The dangers of surfaced information increase to infinity. Data breaches occur almost daily. Personal hackers target information constantly. Your privacy faces new dangers every day.
It requires meticulous planning and methodical actions to erase one’s digital footprint. One must know where the data actually exists and how to remove it efficiently. The complete procedure takes time and calls for dedication. For many, this task is considered overwhelming. Your information is spread through so many platforms. Social media posts can really say a lot. Unused accounts might reveal what old data is still out there.
This guide shall help in protecting your privacy. Practical steps will remove data from different parts of life. Essential tools for privacy will be discussed. We are here to minimize your digital presence. All aspects of online privacy are covered. Discover new methodologies of security. The guide offers tested solutions. Let’s get started on that journey toward digital privacy.
What is a Digital Footprint?
A digital footprint consists of almost every trace you leave online. In simple terms: everything you do on the internet. Each time you visit a website, new data is created. Your online activity builds up over time. Software applications can trace your behavioural patterns. Data brokers solely rely on collecting all this interesting information about you. Your data can then remain active for many years. Now let’s take a detailed look at the essentials:
Active vs. Passive Digital Footprints
Active Digital Footprints are those digital traces left intentionally by an individual acting on digital media. Examples of these are social media updates. Communications via email are included. Digital shopping creates a trail of data. Comments left on websites add up too. Passive Digital Footprint comprises those footprints that are not directly caused by the action of an individual. Websites keep track of browser activity. Apps keep records of location data. Device information is logged. Companies collect such data automatically from various sources.
Common Sources of Digital Footprints
Generic website clicks might easily leave traces when digital footprints are involved. Large hoards of data are stored on social media accounts. E-commerce websites keep a record of your tastes and shopping preferences. Email service providers take account of the pattern of messages. Search sites log your queries. Banking apps keep transaction data. Entertainment apps examine your viewing patterns. News sites analyze your reading behaviour.
Types of Personal Information Collected
A multitude of typed forms of data is collected by companies. Names and addresses hold places in storage. Phone numbers lie safe in databases. Browsing histories remain stored on servers. Purchase records make buying habits known. Movements are revealed through location information. Devices have specific details logged regularly. Social connections are now a data-mapped mechanism.
Data Accumulation Over Time
With each passing day, your digital footprint expands. Old posts can be searched for online literally. Comments from the past remain visible forever. Digital footprint data keeps collecting and growing by itself. Personal details are stored in accounts long forgotten. It’s hard to find deleted records from databases. Information travels between companies. Your profile becomes ever more complete.
Real-world Examples
Consider the daily routine that you spend online. Morning news visits score records. Work email leaves its marks. Shopping during lunch adds its chapter. Social media visibility stays. Evening streaming creates a view profile. App usage creates an activity log. Online payment reflects incurred purchasing patterns.
Why Managing Online Accounts Matters
Your online accounts need constant maintenance. Old accounts can pose security risks. Data breaches lead to identity theft. The safety of accounts contributes to your professional image. Future troubles start with present negligence.
Risks of Abandoned Accounts
Security weaknesses come with forgotten accounts. These inactive profiles are often targeted by hackers. The old passwords may not stand up to today’s protection. Unused accounts may carry outdated personal information. Your information could still be threatened. It is possible for companies to sell these old bits. Security breaches target dormant accounts. These links also lead to active ones. Criminals frequently exploit the connection. The longer you wait, the harder it becomes to recover your account..
Personal Information Vulnerability
Your data is under constant threat. Digital footprint information is uncontrolled in its spread. Old accounts expose one’s personal details, augmenting the probability of their being added to by hackers colluding the given information from various sources. With every breach, your privacy is lessened. Your contact details could be made public by accident. Financial information could remain somewhere in the old system. Medical data could get exposed. Personal photographs are still on the Internet. Your location history is still being recorded.
1. Identity Theft Concerns
It initiates from exposed data. Criminals compile profiles based on old accounts. They target out-of-sight login credentials. Your personal information covers the way for fraud. Some security falls on bank accounts. Credit scores might just face sudden drops. Hackers can forge hot identities. They settle the scores using your info. Recovery takes a lot of time. Stolen identities cause a lot of legal troubles.
2. Professional Implications
Old accounts affect job prospects. Employers check for evidence of a digital presence repeatedly. Social media posts can make or break a career. Profiles from outdated days can damage your professional image. Your continuous attention is needed for your reputation. Your work history soon becomes a matter for public consumption. The former things continue to be viewed by your professional contacts. Career opportunities depend on presence. Digital cleaning enhances your chances of getting a job. Maintenance of professional networks is essential.
3. Future Impact Considerations
Accounts today will impact opportunities in the future. Digital footprint expansion never stops. The value of privacy increasingly becoming a concern. New threats arise daily. Your data now gains value every year. Developments in technology develop new threats. Future employers tend to look at the history of presence. Digital impact on personal relationships. Financial opportunities build on history. Long-term effects have to be reckoned with.
4. Privacy Rights and Regulations
Many Laws safeguard your digital rights. Data brokers must comply with law. You can ask for data deletion. Privacy laws globally continue to expand. Consent means something in the law. Companies have to keep user data safe. Your control options come from regulations. There are penalties for privacy violations now. User rights grow stronger every year. Protection through laws applies to anything digital.
Understanding Search Engines and Your Privacy
The masses of personal data are held by the various search engines. Every Google search creates new records. Your searches disclose personal trends. With every query, privacy concerns arise. The search history creates in-depth profiles.
1. How Search Engines Store Personal Data
All queries are recorded with the search engines. Your browsing history is stored in databases. Automatic storage of location data. Personal interests are revealed by search patterns. Google search saves information about the device. Timestamp for each search. Authentication details link search history. Advertisers have access to your search patterns. Previous queries are used to produce search suggestions. Your data is for targeting advertisements. Search engines are connecting more and more devices. It becomes more detailed by developing user profiles.
2. Impact on Personal Privacy
Your personal searches reveal intimate details about you. Searches about medicines indicate what health concerns you may have. Shopping searches indicate your plans for purchases. Location search reveals travel interests. Online activity creates behaviour patterns. Search data builds user profiles. Personal trends become visible easily. Companies analyze search patterns deeply. Your interests get mapped regularly. Search data affects advertisement targeting. Privacy gaps are widening as searches keep increasing. Tracking becomes more sophisticated daily.
3. Google’s Privacy Policies and Settings
Google has now given privacy controls. The search history can be deleted by users. It can then manage the digital footprint. Privacy settings must be updated regularly. Google records data about users signed in. Anonymously browsing means tracking is limited. The settings related to location history should be under review. Activity controls are the major outline of data collected. Privacy dashboard information on what is still stored. The data can be tailored in different ways by the users. Setting updates has been endless. There are many more options for control.
4. Alternative Privacy-Focused Search Engines
Private search engines provide user protection. DuckDuckGo prevents any tracking of its users. Startpage gives Google results privately. Brave Search maintains user confidentiality. These engines minimize all stored data. Therefore, even your digital footprint remains small. Any search history remains confidential. Location tracking is automatically disabled. User profiles remain anonymous all the time. Advertisers glean little information. Privacy is truly a prime consideration. The quality of the search continues to improve.
5. Search History and Personal Profiling
User personalities are revealed through search patterns. Companies keep detailed profiles continuously. Marketing data is created from one’s interests. Online activity creates segments of users. Reflecting personal behavioural patterns, data reveal general life patterns. The timing of a search indicates an individual person’s day. Types of queries regarding shopping and certain interests give education levels. Types of shopping searches may ascertain income levels. Location queries often show travel. Personal profiles are built increasingly. Data analysis can be more accurate. Profile sharing affects privacy.
6. Removing Personal Information from Search Results
Data removal can be requested by users. Search sites have to follow rules to keep it. Removal processes need quite some patience. The rights of the law support deleting data. Google now accepts requests for removal. Protection needs to be provided to personal information. Provide outdated content for deletion. Tools of privacy assist in removals. Monitoring processes help remove dirt. Documents support requests for removal. Sometimes, the help of a professional can pay off. Variability rates are significantly different.
How to Begin Erasing Your Digital Footprint
It needs a systematic approach to erase the digital footprint. Name of privacy tactics is the result of proper planning. It starts from data assessment through average. Protection strategies are essential at this point. Nothing can make success as thorough work can.
A. Initial Assessment of Online Presence
Begin a full scale search on the internet. Type your name in the search engine. Find some personal information online. Check the results of the image search very carefully. It requires depth and thoroughness in Digital footprint assessment. Need to review social media profiles. Require checking old forum posts.
Then evaluation of professional profiles. Inspection of a business directory. News mentions online. Traces of online activity. Thorough review of public records databases
B. Account Audit and Inventory
Make an online search-wide complete, and input into search engines your own name. Seek personal information online. Check image search results carefully. Digital footprint examination requires thoroughness. Look for a review of social media profiles. Find old forum posts. These too should be assessed: professional profiles.
Business directories check carefully, as well as online news mentions. Online activity traces need to be found. Review public records databases thoroughly.
C. Privacy Settings Optimization
Check all your privacy settings thoroughly. Deny all public access now. Alter access settings on social media for viewing your profiles. Change Google’s privacy settings today. However, Online activity must be regulated. Set strong limits on your accounts right now.
Consider enabling the two-factor authentication. Make it difficult to search for your profiles. Use the different checkup tools for privacy regularly. Reducing the Digital footprint starts here. Implement maximum privacy limitations right at this moment.
D. Content Removal Strategies
Reach out to the websites that host personal information. Request for content removal on those platforms. Laws will back up your right to removal. Follow up on those who accepted your request for removal. Social media posts must be scrutinized openly. Go ahead and erase irrelevant personal stuff right now.
Save the relevant content first before deletion. Draw up a schedule for content removal. Then, ensure that removal requests are tracked in an organized fashion. And now, think about professional removal services. Start with content that presents the highest risk. Remove first anything that contains sensitive data.
Struggling with a tarnished online image? Consider content removal services to erase your digital footprint and regain control over your narrative. By addressing negative online content, you can shift the focus back to your brand’s positive aspects, ensuring a more favourable public perception and renewed trust.
E. Tools and Resources
Privately protect oneself by using the software regularly. Try free dark web scan service. An installation of a password manager is imminent. Get the best security software now. Virtual private network adds protection. Data removal tools help greatly.
Increased protection levels come from the privacy browser. Services for account deletions save time. Alerts are provided regularly for identity monitoring. Use secure messaging apps today. Have the privacy tools updated frequently? New protection methods come out constantly.
Step-by-step Removal Process for Erasing Digital Footprint
Begin your exercise of removing your digital footprint today. The process requires careful planning. Here are the exact steps to follow. Protection accrues through proper execution, while success requires a consistent approach.
Step 1: Identify and List
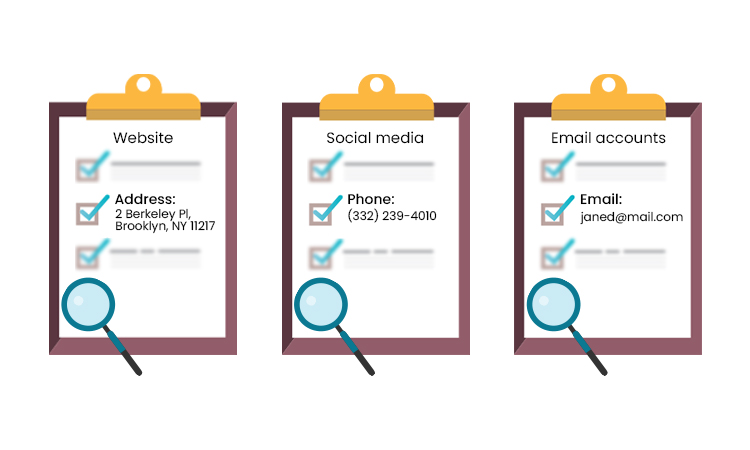
Starting with a thorough data search, list every website that publishes information. Keep a record of social media accounts. Identify which platforms where data can be stored. Check for registrations on email accounts. Then, a spreadsheet for keeping track of all accounts will be created.
Now, follow the inks to locate even more accounts. Dig up all the old email confirmations. There might be online accounts that would take you by surprise. From here, the list can grow rather quickly. Create classifications for the different types of accounts. Removal priorities should be set up right away.
Step 2: Clean Social Media
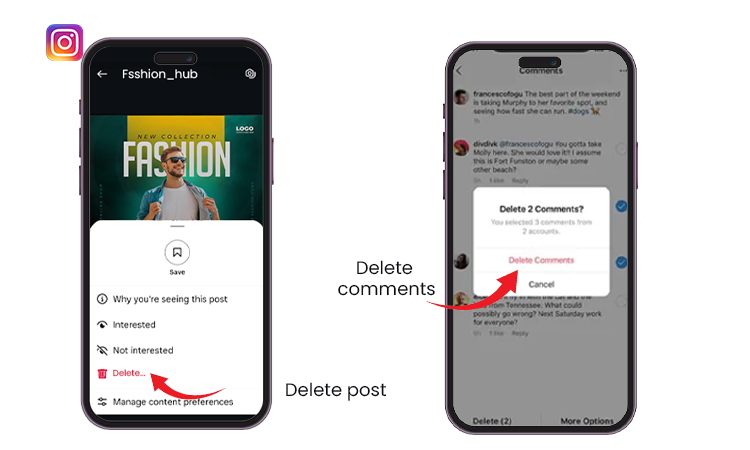
The very first point should always be to scan through all the social media posts thoroughly. Delete all personal information that is deemed unnecessary. Remove all old photographs and comments attached to such photographs. Update privacy settings. Consider the idea of temporary account deactivation. Get started with the oldest first.
Download and save all the most important data to be deleted. Remove tags from other people’s posts. A good, thorough cleanup of one’s digital footprint takes time. For the final check, ensure that all connected applications are also checked for unnecessary app permissions removal. Disconnect third-party application access.
Step 3: Handle Data Brokers
The procedure of getting in touch with leading data brokers has been mentioned. Today, you want that all complete information to be removed. You should follow up on the removal requests. Store your confirmation of removal safely. Have an eye on the process with each broker.
Consider paid removal services. Keep records of all communications extensively. Know your rights to privacy as stated by law. Exercise stubbornness as there are committed data brokers. Submit your identification identity securely. Variation in processing time should be expected. Maintain records of removal requests
Step 4: Delete Old Accounts
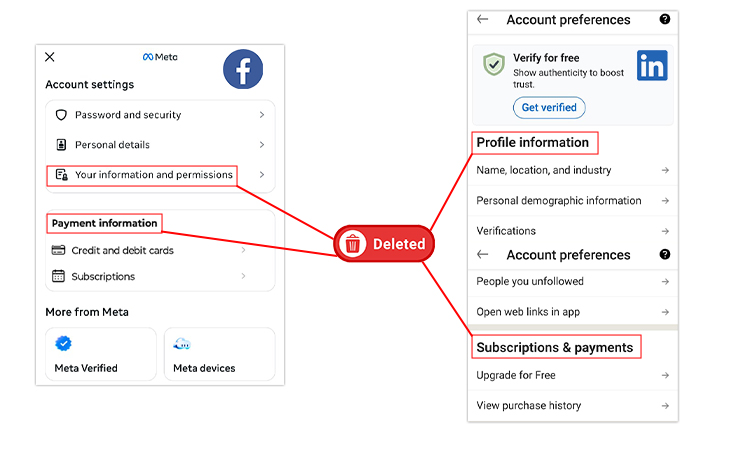
used accounts should be first. Deletion procedures must always be followed. Hold on to any necessary information. Payment info must be deleted right away. Personal information should be deleted in its entirety. Confirm the completion of account removal.
Also, regularly check the status of account deletion. Remove services linked to it. Online activity must be wiped clean. Update password manager records now. Safeguard documents citing account deletions. Maintain deletion confirmation emails.
Step 5: Clean Search Results
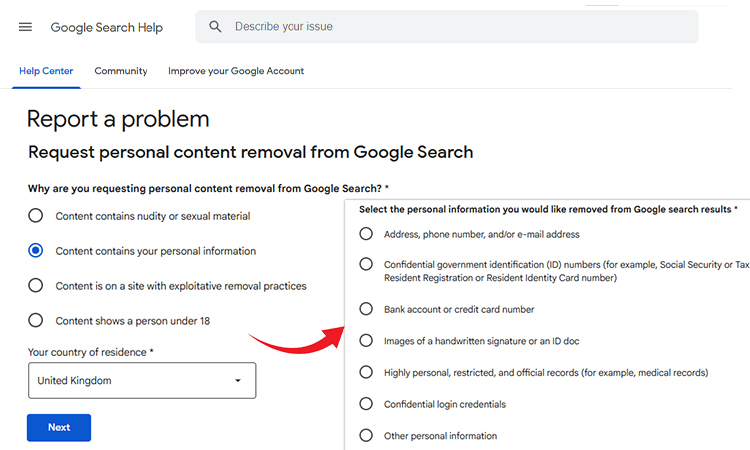
Keep submitting removal requests directly to Google searches. Reach out to site owners to have the content removed. Follow up regularly with the sites. Document the progress of removal requests. Keep a few legal options available. Conduct any communications professionally.
Maintain screenshots as proof of the removed content. Keep monitoring the change in the search results. Regular checks on the search sites are advisable. Repeat removal requests when necessary. Seek professional assistance at times. Be patient with the entire removal process.
Step 6: Maintain Privacy

Formulate new practices of privacy safeguards. Hence, practice virtual private network services. Changing passwords to newer ones is now necessary. Check monthly for privacy settings. Check new data leakage. Identify identity monitoring services.
Keep removal documentation orderly. Regularly schedule checks on privacy. Digital footprint requires constant attention. Protect privacy and be monitored promptly. Was regularly updated from protection tools. Always maintain strong security techniques.
Advanced Privacy Protection Strategies
This needs an advanced solution today. Your digital footprint needs proper protection. It requires advanced privacy-protection methods. New-age threats call for better solutions. Security is standing with the right tools.
1. Browser Security Settings
Browers shall be configured for maximum privacy. Third-party cookies should be blocked right away. Use private mode regularly. Activate the Do Not Track setting. Disable autofill functions now. Install browser extensions focusing on privacy.
Revisit the security settings of the browser given privacy every month. Clear out browsing history regularly. Always use the latest version of browsers. Search for other browsers focusing on privacy. Check thoroughly the permissions of extensions that users add. Observe strict browser hygiene.
2. VPN Usage
Opt for trustworthy virtual private network companies. Use a VPN during online activities. Research and carefully test the security features of a VPN. Configure automatic VPN connections for extra privacy. Check for compliance with the no-logs policy. Choose the right server locations.
Regularly track the VPN system. Update the software immediately. Look for any leak of your IP address. Activate a kill switch feature. Keep renewing your VPN subscription status. Possibly opted for several VPN services.
3. Email Privacy
Take your time and set up different email accounts for different purposes. Use encrypted mail service providers at this point. Enable two-factor authentication at the earliest. Don’t click on dubious links. Check account access logs. Periodically check for connected services.
Do a thorough clean-up of the email folders now. Delete unwanted emails. Change the security settings on your email. Check for emails that have landed in the spam folder. Start monitoring unauthorised access. Strong email habits must be maintained.
4. Social Media Lockdown
Scrutinise all social media accounts. Maximise privacy settings to the best extent. From now onward, limit access to the friend list. Very strictly regulate the visibility of the posts. Check for tagged content regularly. Review connected apps thoroughly.
Purge all unnecessary personal information. Change profile settings every month. Verify location-sharing settings. Review old posts scrupulously. Check the access log from monitoring. Ensure strict posting guidelines.
5. Alternative Privacy Services
Opt for privacy-emphasizing service providers. Switch to secure messaging applications. Use a form of access that stores information in an encrypted format in the cloud. Choose private search engines. Secure yourself by thinking about email providers who take security seriously. To read privacy tool reviews. Monitor service security features.
Update privacy tools regularly. Check the service privacy policies before signing. Verify the security certifications carefully. Keep alternative backup privacy options. Think about paid privacy services.
6. Ongoing Maintenance
Plan routine privacy checks every month. Review the evolution of one’s digital footprint at set intervals. Update security tools in real time. Watch the patterns of access into account. Check any change in privacy settings. Confirm the removal request.
Document the elements of privacy protection. Keep security equipment updated; put in place a protection review. Adapt protection strategies to the new threats. Continue acquiring certifications in security. Develop the habit of doing things that will be an ally for privacy from now on.
Conclusion
Erasing digital footprint requires dedication and time. The procedure requires constant attention. Your privacy is very important these days. Protection starts with knowledge. The digital world is changing quickly. Small steps add up to big changes in privacy. Nurturing this digital garden regularly creates lasting protection. What you do today affects your tomorrow.
Every click you make online creates a digital shadow. Today, every click means permanent traces. Small actions create big privacy impacts. Protection is currently an ongoing effort. The internet recalls everything forever. Data brokers obtain information constantly. Each day, social media reveals personal details. Your digital trail is getting lengthier by the minute. Nowadays, privacy threats arise continually. Technology creates other challenges to security.
Digital interaction is the new normal of modern living. But privacy comes as your birthright. Managing your digital footprint saves your future. Toda, your data needs great defence. The privacy threats are constantly amplifying. Hackers form various new attack patterns. Companies increase their data pools on users. The value of personalities goes up every year. Security measures must be advanced. Protection will always take great vigilance.
You can consider exploring reputation protection services to effectively erase digital footprints. By addressing negative news and enhancing your online presence, these services can help safeguard your brand’s image. Remember, a proactive approach to managing online content often results in a more positive public perception and trust.

